What is AWS Virtual Private Cloud
Amazon Virtual Private Cloud (VPC)
Amazon Virtual Private Cloud (Amazon VPC) lets you provision a legitimately segregated area of the AWS Cloud where you can dispatch AWS resources in a virtual system that you characterize. You have complete control over your virtual networking environment, including the selection of your own IP address range, the building of subnets, and configuration of route tables and network gateways. You can utilize both IPv4 and IPv6 in your VPC for secure and simple access to resources and applications.

You can without much of a stretch alter the network configuration of your Amazon VPC. For instance, you can make an open confronting subnet for your web servers that have access to the web. You can likewise put your backend frameworks, for example, databases or application servers, in a private-facing subnet with no internet access. You can utilize different layers of security, including security groups and network access control, to assist control with getting to Amazon EC2 instances in each subnet.
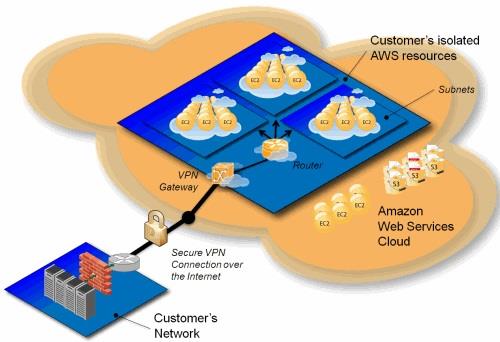
Amazon Virtual Private Cloud (Amazon VPC) enables you to launch AWS resources into a virtual network that you've defined. This virtual network closely resembles a traditional network that you'd operate in your own data center, with the benefits of using the scalable infrastructure of AWS.
Benefits
Secure
Amazon VPC gives advanced security highlights, like security groups and network access control lists, to empower inbound and outbound filtering at the instance and subnet level. Likewise, you can store data in Amazon S3 and restrict access so that it can only be accessible from instances inside your VPC. For extra security, you can make dedicated instances that are truly secluded from different AWS accounts, at the hardware level.
Simple
Make a VPC rapidly and effectively utilizing the AWS Management Console. Select from basic network setups and locate the best counterpart for your requirements. Subnets, IP ranges, course tables, and security groups are created automatically. You invest less time setting up and managing, so you can focus on building the applications that run in your VPCs.
Customizable
Control your virtual networking environment, including the selection of your own IP address range, the formation of subnets, and configuration of course tables and network gateways. Customize the network configuration, for example, by making a public-facing subnet for your webservers that approaches the internet, and putting your backend systems, for example, databases or application servers in a private-facing subnet with no internet access.
Use cases
Host a simple, public-facing website
Host a fundamental web application, like a blog or basic site in a VPC, and increase the extra layers of protection and security managed by Amazon VPC. You can help secure the site by making security bunch rules which permit the webserver to react to inbound HTTP and SSL demands from the Internet while all the while restricting the webserver from starting outbound associations with the Internet. You can make a VPC that bolsters this utilization case by choosing "VPC with a Single Public Subnet Only" from the Amazon VPC console wizard.
Host multi-tier web applications
Host multi-level web applications and strictly enforce access and security limitations between your web servers, application servers, and databases. Dispatch web servers in an openly available subnet while running your application servers and databases in private subnets, with the goal that application servers and databases can't be straightforwardly gotten to from the web. You control access between the servers and subnets utilizing inbound and outbound parcel sifting gave by network get to control records and security gatherings. To make a VPC that supports this utilization case, you can choose "VPC with Public and Private Subnets" in the Amazon VPC console wizard.
Disaster recovery
By utilizing Amazon VPC for disaster recovery, you can have all the advantages of a disaster recovery site at a small amount of the expense. You can occasionally backup critical data from your data center to a few Amazon EC2 instances with Amazon Elastic Block Store (EBS) volumes, or import your virtual machine pictures to Amazon EC2. To guarantee business continuity, you can rapidly launch replacement compute capacity in AWS. At the point when the disaster is over, you can send your crucial data back to your datacenter and end the Amazon EC2 instances that you do not require anymore.
Extend your corporate network into the cloud
Move corporate applications to the cloud, dispatch extra web servers, or add more compute capacity to your network by associating your VPC to your corporate network. Since your VPC can be hosted behind your corporate firewall, you can consistently move your IT resources into the cloud without changing how your clients get to these applications. You can choose "VPC with a Private Subnet Only and Hardware VPN Access" from the Amazon VPC console wizard to make a VPC that supports this utilization case.
Securely connect cloud applications to your datacenter
An IPsec VPN association between your Amazon VPC and your corporate network encrypts all communication between the application servers in the cloud and databases in your data center. Web servers and application servers in your VPC can use Amazon EC2 flexibility and Auto Scaling highlights to develop and contract varying. You can make a VPC to help this utilization case by choosing "VPC with Public and Private Subnets and Hardware VPN Access" in the Amazon VPC console wizard.
Out-of-band and inline traffic inspection
Amazon VPC traffic mirroring copies the traffic, alongside full payload data, from versatile network interfaces (ENIs) of EC2 instances, and conveys it to out-of-band monitoring and security analysis tools.
Amazon VPC ingress routing permits you to easily deploy network and security appliances, including third-party contributions, inline to the inbound or outbound Amazon VPC traffic. Inline traffic assessment encourages you screen and secure traffic to shield your workloads from malicious actors.
Partners
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |