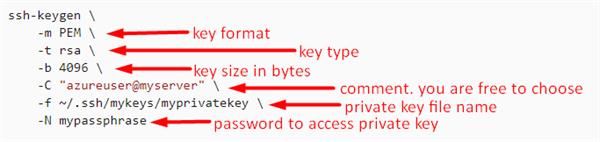
Create a Secured Shell (SSH) key pair in Azure
About Secured Shell (SSH):
- It is an encrypted connection protocol, therefore, protects the communication security and integrity
- It allows secure and strong connection over an unsecured connection
- It helps to eliminate the requirement of password for the sign-in process, but it shares the private key
- It is default connection protocol for Linux virtual machines hosted on Microsoft Azure
- Mainly used for secure remote login from one computer to another computer.
How do SSH works?
Thus, SSH follows the client-server model so the request goes from SSH client to SSH server via a secure channel. The SSH uses public-key cryptography to get it verified on the SSH server.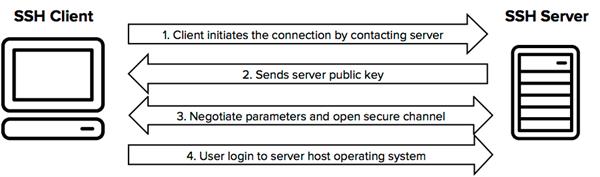
Image resource: ssh.com
Pre-requisites:
- Azure CLI (Bash) [>_] in Azure portal
- Or https://shell.azure.com
- Azure Subscription (Pay as you go or any other)
Original syntax:
Open the Azure Portal and click on the Shell icon [>_] 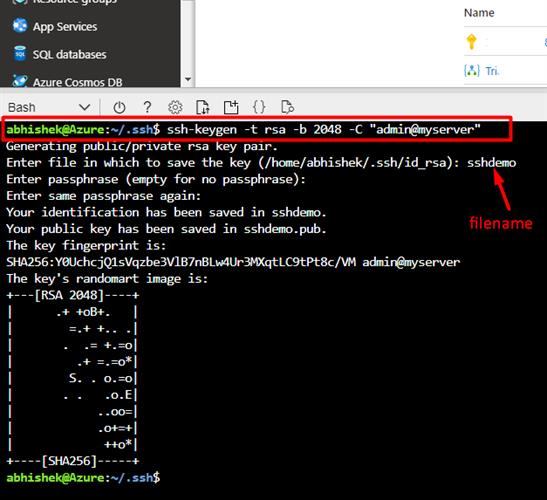
Steps:
Enter the command on Bash prompt
abhishek@Azure:~/.ssh$ ssh-keygen -t rsa -b 2048 -C "admin@myserver"
It will ask for the file name to store the key files
Enter file in which to save the key (/home/abhishek/.ssh/id_rsa): sshdemo
Then, it would ask for the passphrase (password to access the private key file). This should be remembered to the originator for future reference.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in sshdemo.
Finally, the keys will be generated with the <filename.pub> and you will get the below message along with the key fingerprint which is an encrypted format of the key
Your public key has been saved in sshdemo.pub.
The key fingerprint is:
SHA256:Y0UchcjQ1sVqzbe3VlB7nBLw4Ur3MXqtLC9tPt8c/VM admin@myserver
You also can generate the ssh keys at the time of creating Linux virtual machine through Azure CLI. The following command can be used:
az vm create --name VMname --resource-group RGname --generate-ssh-keys
The --generate-ssh-keys flag will create the ssh keys at runtime.
Note: the default location for key files is ~/.ssh directory unless specified. You can use
–ssh-dest-key-path flag to give the custom path.